Firewall and Proxy Server
Firewall :
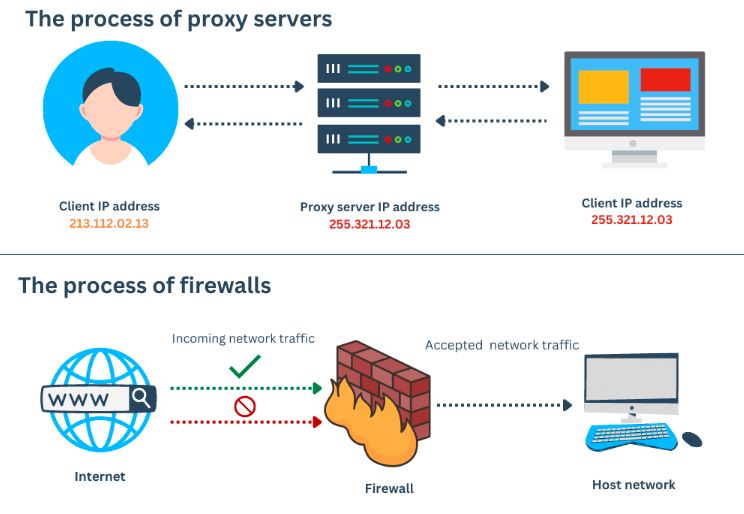
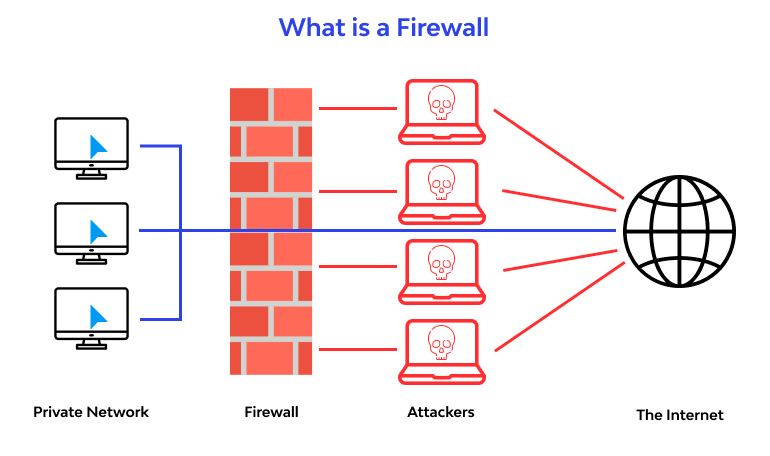
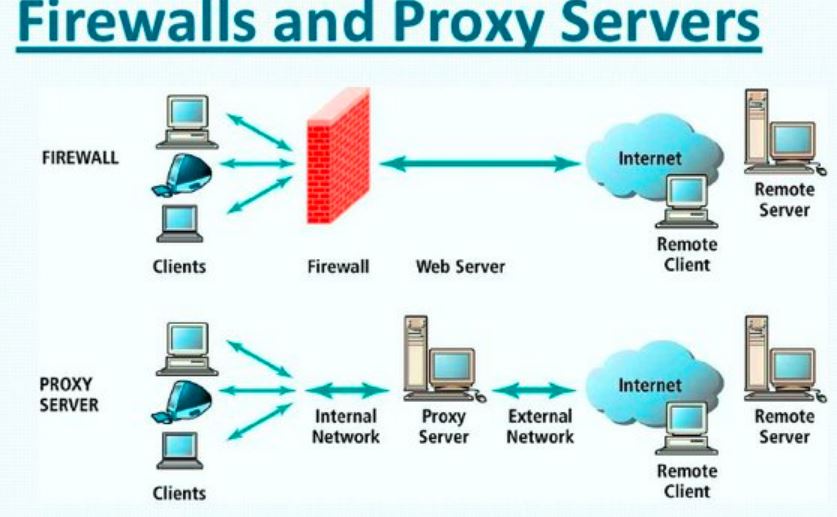
Software known as a firewall prevents unauthorized users from accessing or leaving a private network. All data packets pass through the firewall, which determines their permission to enter or exit the network. All traffic must traverse the firewall, and only permitted traffic can pass through it. Firewall and Proxy Server, the system sits between two networks, enforcing an access control policy between them. It operates on the network layer of the Open Systems Interconnection (OSI) paradigm to encrypt the data before sending it.
Proxy Server :
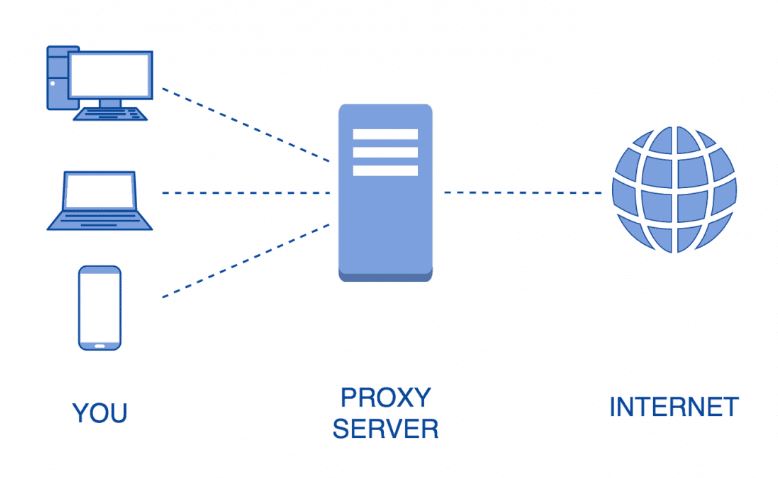
A proxy server is a kind of server that helps connect any device to the rest of the internet by acting as a gateway or middleman between the two. A proxy is one that receives connection requests, passes them, and then delivers data for those requests. Firewall and Proxy Server Because it conceals the client’s IP address by using the anonymous network ID rather than the client’s real IP address, it is able to prevent the client’s actual IP address from being disclosed.
Difference Between Firewall and Proxy Server–
| Firewall | Proxy Server |
| It stops users from connecting to unapproved networks. | It streamlines the process of connecting across a network. |
| The firewall has the ability to monitor and filter all of the traffic that is coming into and going out of a particular local network. | A proxy server links an external client and a server so they can interact. |
| It does this by monitoring the IP packets that are traveling via the network. | The client-side requests that are made to join the network are filtered according to its criteria. |
| This interface connects both a public network and a private network. | It is possible to use public networks on both sides. |
| It incorporates data from both the network and the transport layer. | It operates on the application layer’s data. |
| It serves to protect an internal network from attacks. | To conceal one’s identity and circumvent constraints, it is used. |
| It operates at the packet’s level. | The system operates at the application protocol level. |
Read also : Key Components of a Computer Network, What are The Different Components of a Computer Network ?(Lession- 22)

Hi, I’m Narinder Kumar, founder of BlogsBuz.com. I create articles and generate celebrity biographies, providing verified, up-to-date content. As an SEO expert and online tools creator, I also share practical tips on making money online, finance management, blogging, and passive income. My mission is to provide accurate information and keep you away from fake content, ensuring you stay well-informed and make smart decisions online.